Detect, respond, and contain
before damage is done.
While offensive testing reveals vulnerabilities, defensive services ensure you can detect and stop real threats in real time. Our team helps you build a resilient security posture that protects your systems, data, and people — 24/7.
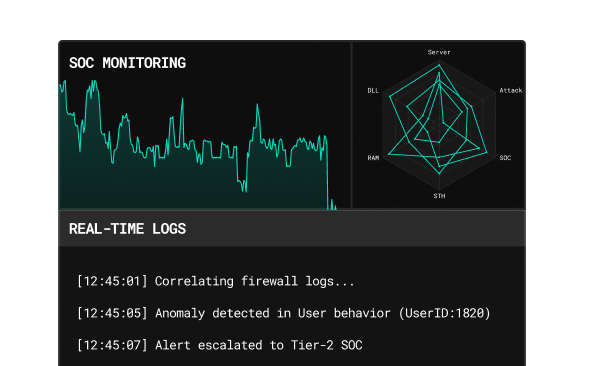
Know what's happening - when it happens
With SOC as-a-service, your environment is constantly monitored by analysts and machine intelligence. We correlate logs, detect anomalies, and escalate real incidents before damage spreads. You get a real time situational awareness - without building an internal SOC from scratch.

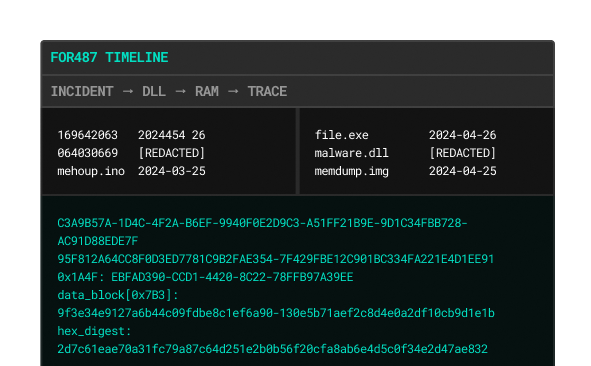
Every trace tells a story - we reveal it
Our forensic experts reconstruct the full attack timeline across endpoints, memory, and logs. From reverse engineering binaries to identifying root causes, you gain legal-grade visibility into the "how" and "why" of every incident. Evidence-based, chain of custody secured.
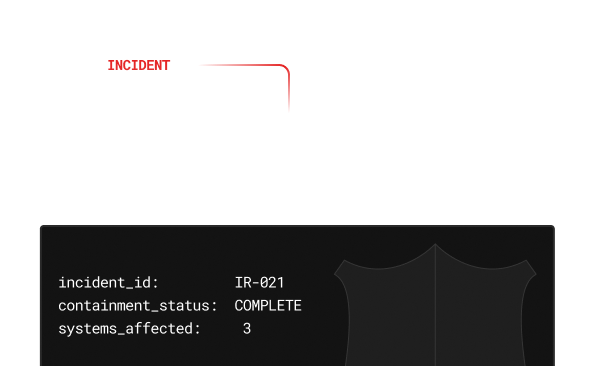
Act fast,contain threats, and bounce back stronger.
When breaches happen, seconds matter. Our IR team isolates affected systems, removes persistence, and guides your recovery - fast. After the smoke clears, we refine detection rules, run tabletop exercises, and leave you with stronger incident playbooks.
Defensive Services
Our defensive security services help you build a resilient security posture that can detect, respond to, and recover from cyber threats effectively.
SOC-as-a-Service
24/7 security monitoring and threat detection with real-time alerts and incident response capabilities.
Digital Forensics
Comprehensive digital crime scene investigation to identify root causes and preserve evidence.
Incident Response
Rapid threat containment and recovery with structured response procedures and clear communication.
Reverse Engineering
Analyze malicious code and understand attack techniques to improve defensive strategies.
Risk Assessment
Comprehensive evaluation of security posture and identification of potential vulnerabilities.
Shield Tech Academy
Built for the Real World
From zero to expert. Get trained by working professionals in offensive security, digital forensics, and more.
Shield Tech Academy
Built for the Real World
From zero to expert. Get trained by working professionals in offensive security, digital forensics, and more.

Feedback from our clients
Our specialization implies strict client confidentiality so all our projects are under NDA and will never be shown without the client's permission or request.
Shield Tech Hub’s team helped us uncover and fix critical vulnerabilities in our hotel PMS system. Their professionalism and speed were impressive.
Their red team service was game-changing. It gave us a realistic assessment of our product compliance readiness. Highly recommend for any health or hospital institue
We sent our security team through their academy for capacity building. It wasn’t just training—it was transformation.
Shield Tech Hubs Team built our Security Operational Center(SOC) they are extremely experienced and ready to respond incidents in timely fashion.
The defensive security measures implemented by Shield Tech Hub have significantly reduced our attack surface. Excellent results.
They gave us a Tripple A Vulnerability Assessment and Penetration Services VAPT, There was no downtime and uncovered alot of vulnerabilities

Let's Talk Cyber
Tell us what you need. We'll build it, train it, secure it.