Simulate the threat
before it strikes.
Our team of experts are dedicated to developing cutting-edge software solutions that provide the ultimate protection for your digital assets.
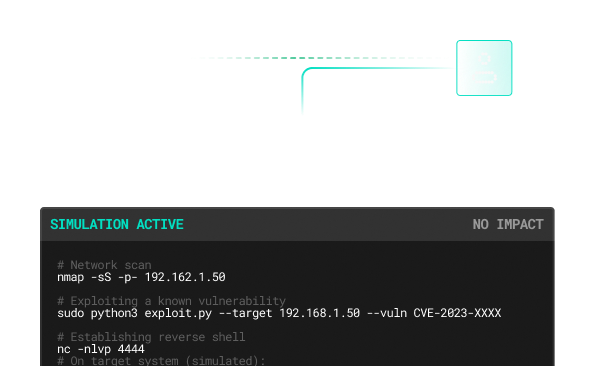
Specialized Cybersecurity Services
Our red-team operators deploy the same multi-vector tactics, techniques, and procedures (TTPs) used by nation-state and ransomware groups—across network, cloud, and human layers. You witness how an attacker would breach, pivot, and exfiltrate data end-to-end, but in a fully controlled, no-impact environment. The result: a crystal-clear view of your true exposure, not a sanitized lab test.
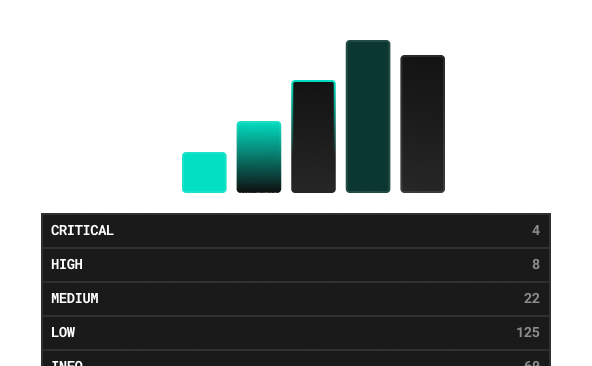
Deep Vulnerability Insights
Every finding comes with context, not just CVE IDs. We correlate exploitability, business impact, and lateral-movement potential to give each weakness a risk score that executives and engineers can both act on. Interactive dashboards, executive summaries, and step-by-step remediation guides help your teams fix root causes fast—eliminating guesswork and "scan fatigue."
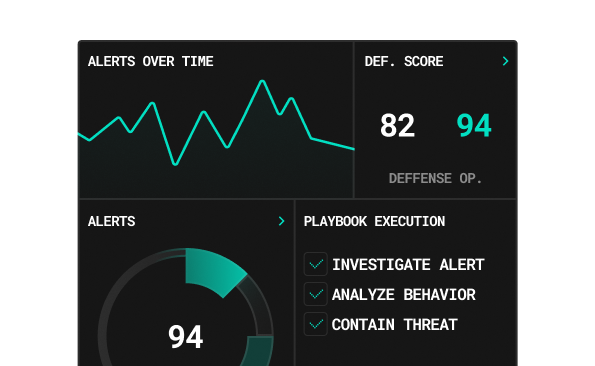
Specialized Cybersecurity Services
Our red-team operators deploy the same multi-vector tactics, techniques, and procedures (TTPs) used by nation-state and ransomware groups—across network, cloud, and human layers. You witness how an attacker would breach, pivot, and exfiltrate data end-to-end, but in a fully controlled, no-impact environment. The result: a crystal-clear view of your true exposure, not a sanitized lab test.
Offensive Services
Our specialization implies strict client confidentiality so all our projects are under NDA and will never be shown without the client’s permission or request.
Penetration Testing
Ethical hacking to uncover system flaws before attackers do. Web, network, mobile — tested under real conditions.
Vulnerability Assessment
Comprehensive scanning and analysis to detect known weaknesses in your digital infrastructure.
Red Teaming
Simulated full-scope cyberattacks to test detection, response, and overall resilience under pressure.
Web & Mobile App Testing
In-depth assessment of your web platforms and mobile apps using OWASP methodologies.
IoT Security
Test the firmware, APIs, and ecosystem around your connected devices — from smart sensors to industrial machines.
Social Engineering
Evaluate how vulnerable your human layer is to manipulation and deception techniques.
Cloud Security Testing
Identify misconfigurations, privilege escalations, and insecure APIs across AWS, Azure, or GCP.
Shield Tech Academy
Built for the Real World
From zero to expert. Get trained by working professionals in offensive security, digital forensics, and more.
Shield Tech Academy
Built for the Real World
From zero to expert. Get trained by working professionals in offensive security, digital forensics, and more.

Feedback from our clients
Our specialization implies strict client confidentiality so all our projects are under NDA and will never be shown without the client's permission or request.
Shield Tech Hub’s team helped us uncover and fix critical vulnerabilities in our hotel PMS system. Their professionalism and speed were impressive.
Their red team service was game-changing. It gave us a realistic assessment of our product compliance readiness. Highly recommend for any health or hospital institue
We sent our security team through their academy for capacity building. It wasn’t just training—it was transformation.
Shield Tech Hubs Team built our Security Operational Center(SOC) they are extremely experienced and ready to respond incidents in timely fashion.
The defensive security measures implemented by Shield Tech Hub have significantly reduced our attack surface. Excellent results.
They gave us a Tripple A Vulnerability Assessment and Penetration Services VAPT, There was no downtime and uncovered alot of vulnerabilities

Let's Talk Cyber
Tell us what you need. We'll build it, train it, secure it.