Know the threat
before it knows you.
Our cyber intelligence stack gives you visibility into dark web chatter, brand impersonation, exposed credentials, and infrastructure targeting—long before attackers strike. Stay proactive, not reactive.
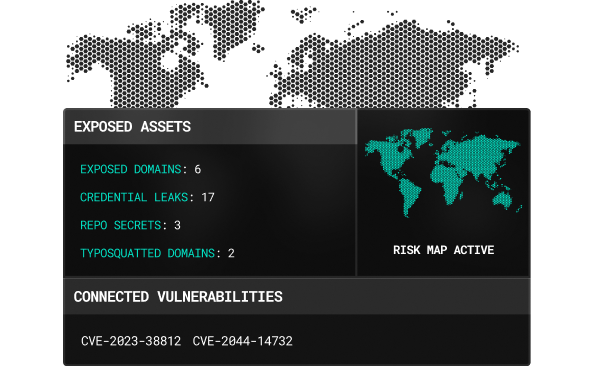
See your exposure from an attacker's perspective.
We map what adversaries see - domains, IPs, user accounts, Github leaks, CVEs, - and give you a clear view of your external footprint. This isn't guesswork. This is how attackers choose their targets.
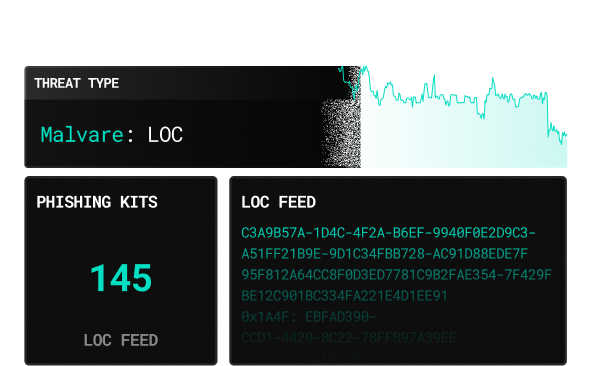
Stay ahead of fast moving adversaries
We collect, enrich, and deliver contextual threat feeds - from malware hashes and phishing kits to infrastructure ovelaps and deep/dark web chatter. All mapped to tactics you can defend against.
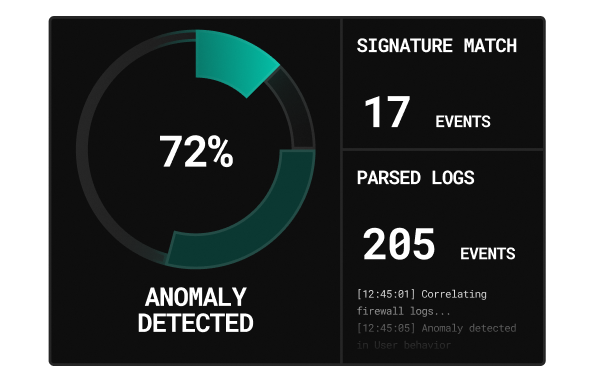
Find what others miss.
Our hunters analyze behaviours,anomalies,and log artifacts across your stack to reveal persistent, low-noise threats - before they activate. We don't wait for alerts.We find them.
Intelligence Services
Advanced blue/black/grey, human-verified context. Actionable outcomes.
OSINT Monitoring
Open source intelligence, dark web, and credentialed collections.
Dark Web Monitoring
Search for your assets, credentials, and brand exposure in black markets, forums, and breach dumps.
Brand Intelligence
Monitor for brand impersonation, phishing, and reputation risks across the open and dark web.
Threat Intelligence
Actionable threat feeds, IOCs, and TTPs tailored to your environment and industry.
Threat Hunting
Proactive search for hidden threats and adversaries using advanced analytics and expert analysis.
Shield Tech Academy
Built for the Real World
From zero to expert. Get trained by working professionals in offensive security, digital forensics, and more.
Shield Tech Academy
Built for the Real World
From zero to expert. Get trained by working professionals in offensive security, digital forensics, and more.

Feedback from our clients
Our specialization implies strict client confidentiality so all our projects are under NDA and will never be shown without the client's permission or request.
Shield Tech Hub’s team helped us uncover and fix critical vulnerabilities in our hotel PMS system. Their professionalism and speed were impressive.
Their red team service was game-changing. It gave us a realistic assessment of our product compliance readiness. Highly recommend for any health or hospital institue
We sent our security team through their academy for capacity building. It wasn’t just training—it was transformation.
Shield Tech Hubs Team built our Security Operational Center(SOC) they are extremely experienced and ready to respond incidents in timely fashion.
The defensive security measures implemented by Shield Tech Hub have significantly reduced our attack surface. Excellent results.
They gave us a Tripple A Vulnerability Assessment and Penetration Services VAPT, There was no downtime and uncovered alot of vulnerabilities

Let's Talk Cyber
Tell us what you need. We'll build it, train it, secure it.